

FUTO is the greatest use of on-device LLM so far. It never gets anything wrong, even my thought markers “…”


FUTO is the greatest use of on-device LLM so far. It never gets anything wrong, even my thought markers “…”


I assume the problem is hardware. Matt’s hardware didn’t work well with LM, therefore Matt thinks LM sucks… I do wish there was better hardware support but it’s the reason apple went with 1 product = 1 OS = 1 general set of hardware. Sure not every iPhone has the same hardware, but that’s why they have the model numbers, and it’s so much easier to test 200 model mixes than 2,000,000 (Android). Windows gets all the debug info sent directly to them like the others but they also have a huge stack of hardware they can use or they can buy it to test.


Just something to keep in mind for those not in the security space. When a security company does an audit, its generally a checklist of commercial and custom security software along with a couple people poking around looking for more manual harder to find stuff. But there’s a reason companies like Mullvad have a bug bounty program… Just because cure53 didn’t find it, it doesn’t mean some bored hacker won’t…
Absolutely better than nothing though.


This should have been much more well thought out The wording, image, buttons, specific wording for each page.
They really screwed the pooch.
Another 4-6 months minimum before release. But quarterly numbers must be met.
Good stuff. Not thought about enough. GPS spoofing random routes also.
Do a lot of reading. Get a cyber informations systems basics overview on your own self-teaching before you try to understand it all.
Stay away from session and matrix. Signal, Nostr, SimpleX (nvm if you use Apple products) and the like are okay, but they are all hobbyist influencable products besides Signal which gets fat government grants and just happens to use the same encryption standards as all other huge name E2EE tools.
Stuff is fun to learn on, but get a good VPN (debates about… mullvad, ivpn, cryptostorm seem okay). here’s something fun for you and free: https://www.thc.org/segfault/
Then maybe you’re okay.
A number of people can see your IP, people will chime in and add to ane remove from this list:
Some info may be wrong. But having someone’s IP in the days of routers and all filtered ports means little, unless you piss off someone who knows some low level customer support person @ your ISP to pay to get your account info. Or you’re dealing drugs in which case use TAILS and stop fucking with technologies you don’t know the specifics of.
If they knock you offline and you can’t access anything at all, unplug your router AND MODEM (most importantly your modem) for an hour. Go touch grass for an hour. Widdle a wee branch. Plus your boxes back in and you’ll be bright as new.
@possiblylinux127@lemmy.zip this isn’t meant to be a dig at you, although last time you didn’t care to correct or learn if I recall,but often times you leave out the “if so,” “possibly, what and XYZ?'” and it ends up spreading misinformation because you didn’t know enough or care enough to type enough.
I love Matrix but we need to be open about what the fish is before skinning it…
https://gist.github.com/maxidorius/5736fd09c9194b7a6dc03b6b8d7220d0
https://blog.erethon.com/blog/2022/07/13/what-a-malicious-matrix-homeserver-admin-can-do/
https://www.reddit.com/r/PrivacyGuides/comments/q7qsty/is_matrix_still_a_metadata_disaster/
Just to confirm the obvious. Downvotes are expected but OP you should read this.
They are close enough to see that they are quad copters, and they make a buzzing noise, correct?
There have been a lot of UAP flaps where the objects (not quad copter looking) will fly low over the countryside, just above the tree-lines to much higher. They usually make no noise aside from reports of static or screeching or electronic interference.
Unlikely to be the case but if so, report to your countries MUFON type department and get as much evidence (video with sound, drawings, time and date, etc) as you can.
There is something else out there, whether it’s military black projects mapping areas or what have you, and it needs to be documented.
If it is for sure quad copter drones, you can get a device to blast the 2.4Ghz spectrum for a short time and make them ‘phone home’ and the operators will stop flying them over your property once they realize something wrong keeps happening when they do. Legality varies.
Many tutorials available to DIY. You can also buy them pre-built, just more expensive.
wget toteslegitdebian.app/installer.sh & chmod +x && ./installer.sh
was I not supposed to do that? but staxoverflown said it’s OK.


That does go a long way towards explaining why there are so many Bluetooth vulnerabilities, thanks for the info. Looking at the list of Bluetooth protocols wiki page gives me a headache. Surely there is a better standard, and I see things like HaLow, ZigBee, Z-Wave and other custom protocols, but it seems like there should be a very cleanly well-documented alternative to do the basics that everyone expects BT to do. This, coming from a total noob, speaking completely out of my anus. I just know that as a BT user, it’s a crapshoot whether there will be major audio delay, and pause/play actually worked, that’s if pairing works in the first place. But if something did come along I wonder if there would even be adoption among consumer devices.


Is it true the Bluetooth network stack is larger than the WiFi network stack? If so, why? I don’t know much about BT besides pairing, allowing calls and audio in/out, transferring files, and… is there more? It takes a day of reading documentation to understand all the advanced options on my ASUS router interface, and that’s without anything proprietary.
I’m just surprised and curious and never got a satisfying answer.


That’s true, there is the Scunthorpe problem. I guess we’re just doing another 20 year cycle like we have for all of civilization. If someone centuries in the future finds this comment chain, please name the solution to your 20 year repeating fractal math problem something like the CockSyn Solution. I want to be like Shadow from American Gods. Or more accurately like Pythagoras with his stealing murder cult.


Can any late teen-early 20s armchair philosophers once-over this for me?
I have a theory. Never before on the internet (going on 30 years of it) have I seen so many curses used but not fully spelled out (‘f*ck’ for example).
I believe the change has to do with social media and specifically short-form video apps (Tiktok, IG Reels, Youtube Shorts) - not all of which I am familiar with, but I know at least YT and I believe TT does as well. When curse words or words like rape and murder are used in text (or ‘subtitle’ text on screen) the video reach can be penalized in some way. I assume it’s similar in comments.
So you have a ton of the younger generation consuming hours each day of censored curse words, and in their mind it becomes just what you’re supposed to do, socially. They end up doing it with each other over text, and consequently in comments. I have a younger co-worker who will gladly say “F*ck that dude hes a b*tch” in group chat, and when I asked him why he doesn’t just say the words he’s using, he said “I just don’t like to curse.” Which makes no sense to me, as it’s the same word and intent.
I know some Lemmy instances will remove words, but generally only ‘bitch’ and derogatory slur words.
So I hypothesise it’s simply unexamined social conditioning, where they see their peers doing it so they do it too, never questioning why.
Yeah but he’s just a temporarily inconvenienced billionaire, the rest of these welfare queens are out here collecting rent and sitting around all day. They don’t need the money like he does. As soon as he gets a job, he’ll hustle that first billion in no time.
His YouTube shorts (500/day goal) is videos of Elon musk saying things, with the background music alternating between the sigma male tune and the movie clip tune.
Did you see how ELON MUSK OWNED💯 DON LEMON by getting flustered at the question of “half your advertisers have left the platform, if X fails, isn’t that on you?” so he told Don he should choose his words carefully because the interview clock only had 5 minutes left? And then Don was OWNED because he rephrased the question?
LMAO. SUCK IT CNN. OWNED!


So programming is gonna go from a “search, understand basics, copy/paste, make changes” industry to a “I breathe compiler optimization, pay me money” industry?
Can’t say I’m that upset, it had to happen eventually. But this will only kick the brainpower down the road for the copy/pasters because they’ll have a lot more time to dig in and specialize.
Lemmy is reddit 3.0. Early on, Reddit was basically only a website for tech nerds and misfits; atheism and jailbait were some of the most visited subreddits, idpol and divpol weren’t a make-or-break-your-family issue back then but there were still a ton of terminally online furries (yes if you’re a furry you’re weird, but weird is fine, let that freak flag fly.) I’m including myself in the group of outcasts and misfits, and my freak flag flies in weird ways too. I’ve been on Reddit since the default UI was 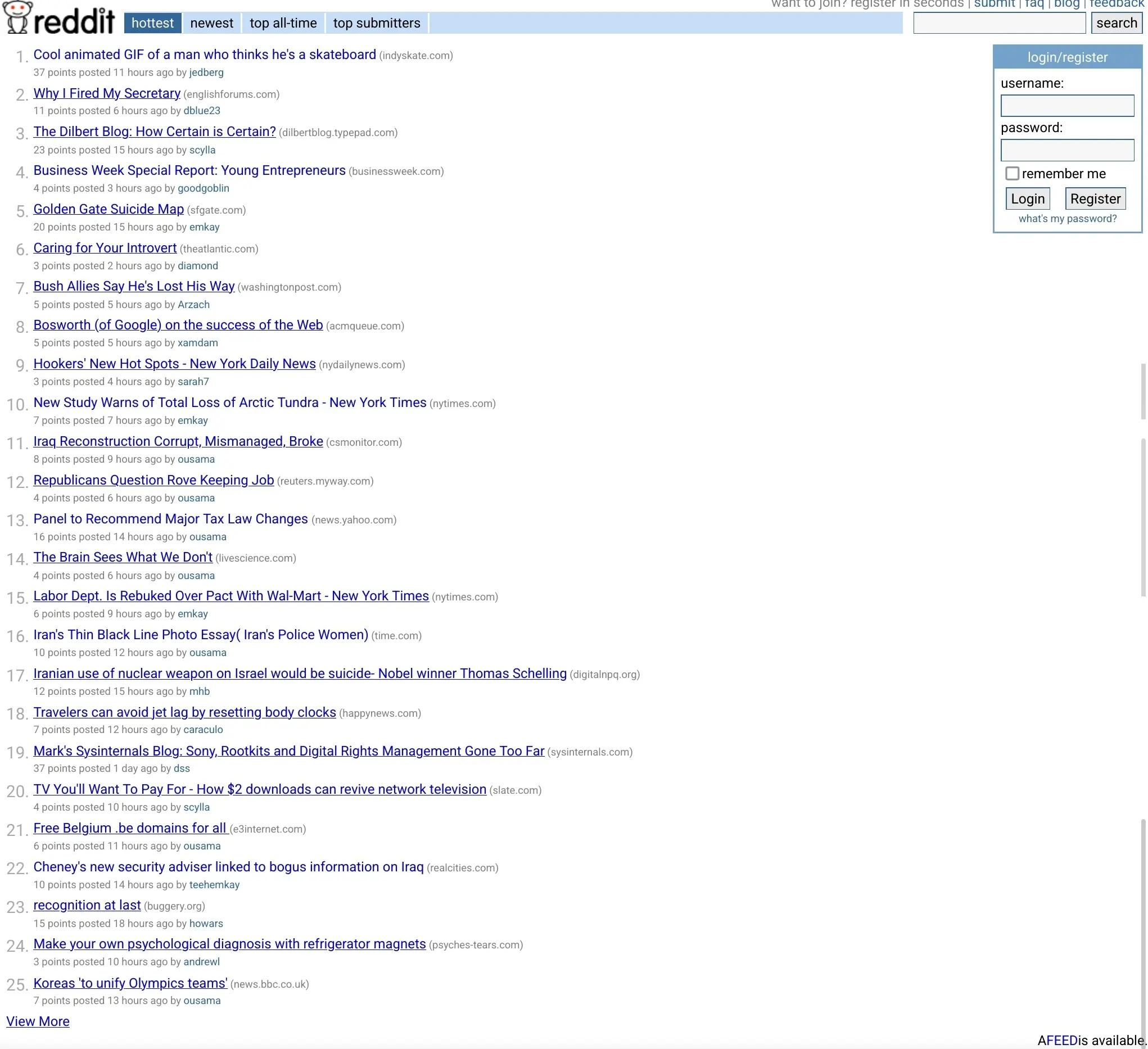 , although it hadn’t changed much over the years before the redesign. Notice the quality of submissions though - it was a place for the intellectually curious.
, although it hadn’t changed much over the years before the redesign. Notice the quality of submissions though - it was a place for the intellectually curious.
But you have a large subset of users who use pedantry and grammar nazi`ism as a way to feel powerful when they’re powerless. It’s like picking on those lower than you, when you’re in the bottom of the pecking order.
Those people saw reddit go from their bastion of freedom to the corporate ad-haven it is today and all came here. You also have a lot of younger people with the time to kill and are just trying something new.
That was supposed to be or, not of.
In turn it compromises ssh authentication allows remote code execution via system(); if the connecting SSH certificate contains the backdoor key. No user account required. Nothing logged anywhere you’d expect. Full root code execution.
There is also a killswitch hard-coded into it, so it doesn’t affect machines of whatever state actor developed it.
It’s pretty clear this is a state actor, targeting a dependency of one of the most widely used system control software on Linux systems. There are likely tens or hundreds of other actors doing the exact same thing. This one was detected purely by chance, as it wasn’t even in the code for ssh.
If people ever wonder how cyber warfare could potentially cause a massive blackout and communications system interruption - this is how.
I don’t know why but I’ve got this strange tingling feeling it might just be a human nature group thing.